IOC Hunter Feed
Access our IOC Hunter feed through our API endpoint.
This document describes the JSON structure of the IOC Hunter feed, which provides threat intelligence data, including indicators of compromise (IOCs) and associated threat actor information. This feed helps enhance cyber threat analysis by integrating publication details with enriched metadata.
How to Access This Feed
-
Open Your Terminal or Command Prompt: This is where you'll type the curl command. On Windows, you can search for "cmd" to open the Command Prompt. On macOS or Linux, you can open the Terminal.
-
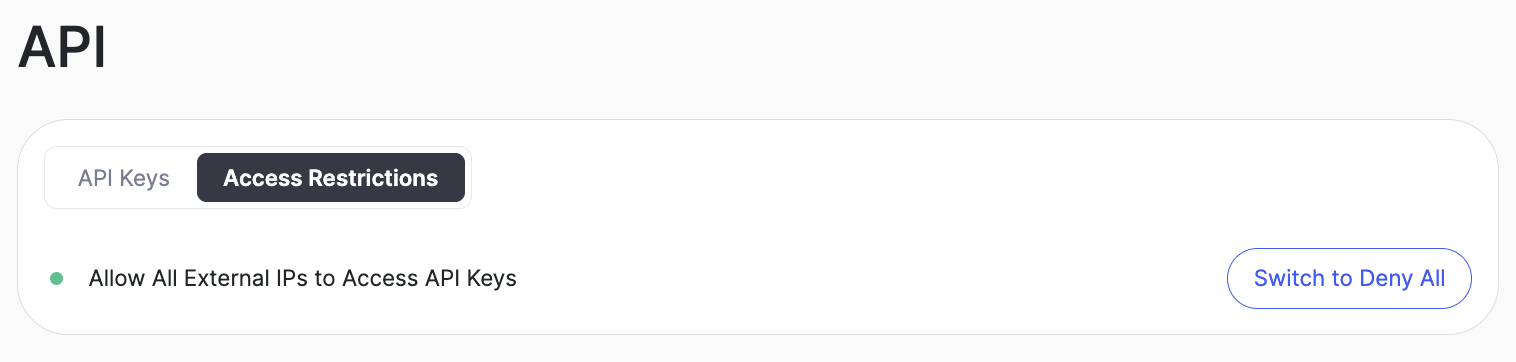
Prepare Your API Key: Before running the command, ensure you have your API key ready. This should be a string of characters you obtained when you created your API key in the previous step. Be sure that API > Access Instructions is set to Allow All. (This is set to Allow All by default)
-
-
Construct the Curl Command: Type the following command, but replace <API_TOKEN_GOES_HERE> with your actual API key.
-
curl -o ioc-hunter.json.gz 'https://api.hunt.io/v1/feeds/ioc-hunter' -H 'token: <API_TOKEN_GOES_HERE>' - Ensure you remove
<API_TOKEN_GOES_HERE>and replace it with your API key without the angle brackets.
-
-
Execute the Command: After typing the command with your API key, press Enter to execute it. This sends a request to the specified URL with your API token for authentication.
-
Review the Response: The server's response to your request will be in a file named
ioc-hunter.json.gz. This contains the data you're requesting from the API—in this case, the IOC Hunter Feed.- Note: Please be aware that the dataset is provided in a compressed format
ioc-hunter.json.gz. For decompression, utilize a native system utility or opt for a verified external tool designed for this purpose.
- Note: Please be aware that the dataset is provided in a compressed format
Optional Query Parameters
You can customize the IOC Hunter Feed results using the following optional query parameters:
| Parameter | Type | Description |
|---|---|---|
days | int | Limits the results to IOCs published within the last N days. Allowed values are: 1, 7, 30, 60, 90, 180, 360, and 720. Useful for narrowing down the feed to recent or extended historical data. |
publication_domain | string | Filters results to a specific publication apex domain (e.g., example.com). This filter is case-insensitive. Useful when analyzing IOCs from a specific trusted source. |
Example Usage
curl -o ioc-hunter.json.gz \
'https://api.hunt.io/v1/feeds/ioc-hunter?days=30&publication_domain=example.com' \
-H 'token: <API_TOKEN_GOES_HERE>'Returned Data
The IOC Hunter feed API returns the following fields when queried. Details on accessing the IOC Hunter feed API can be found here.
| Field | Type | Desc | Optional |
|---|---|---|---|
| ioc_hunter_metadata | array | An array containing one or more entries of enriched IOC data. | True |
| publication_title | string | The title of the publication or article from which the IOC data is derived. | True |
| publication_name | string | The apex domain of the website or source that published the article. | True |
| publication_url | string | The full URL where the publication can be accessed. | True |
| published_at | float (Timestamp) | The timestamp marking when the publication was released or captured. | True |
| threat_actor | object | An object containing detailed threat actor information associated with the publication. | True |
| id | int | A numeric identifier for the threat actor. | True |
| uuid | string | A unique identifier for the threat actor (UUID format), as available. | True |
| origin | string | The attribution to identify the threat actor. | True |
| synonyms | array | A detailed narrative of the threat actor’s activities, targets and motivations. | True |
| description | string | A detailed narrative of the threat actor’s activities, targets and motivations. | True |
| meta | object | Contains additional contextual data such as sponsor, victims, and incidents. | True |
| sponsor | string | Nation state sponsoring threat actor, where available. | True |
| victims | array | Countries targeted by the threat actor. | True |
| category | array | The sectors or industries that are typically targeted by threat actors. | True |
| incident | array | Key motivations for threat actor’s attack. | True |
| ransomware_group | boolean | Indicates whether the threat actor is associated with ransomware activities. | True |
| country_code | string | The country code representing the threat actor's geographical association. | True |
| country | string | The name of the country linked to the threat actor. | True |
| description | string | Short description of the original publication or context in which the IOC was reported. | True |
| malware_name | String | Name of the malware linked to the IOC. | True |
{
"value": "d9e52663715902e9ec51a7dd2fea5241c9714976e9541c02df66d1a42a3a7d2a",
"ioc_type": "ioc_sha256",
"publication_name": "medium.com",
"publication_title": "Shamoon Malware. Shamoon Malware is a wiper that spread...",
"publication_url": "https://medium.com/@cyberecht/shamoon-malware-e24823501b10",
"published_at": "2025-02-28T18:33:00",
"threat_actor": {
"id": 46,
"uuid": "4f69ec6d-cb6b-42af-b8e2-920a2aa4be10",
"name": "APT33",
"origin": "APT33",
"synonyms": "APT 33, Elfin, MAGNALLIUM, Refined Kitten, HOLMIUM, COBALT TRINITY, G0064, ATK35, Peach Sandstorm, TA451",
"description": "Our analysis reveals that APT33 is a capable group that has carried out cyber espionage operations since at least 2013. We assess APT33 works at the behest of the Iranian government.",
"meta": {
"sponsor": "Iran (Islamic Republic of)",
"victims": [
"United States",
"Saudi Arabia",
"South Korea"
],
"category": [
"Private sector"
],
"incident": [
"Espionage"
]
},
"ransomware_group": false,
"country_code": "IR",
"country": "Iran",
},
"description": "The post discusses Shamoon malware, a wiper that targets devices on a shared network to erase operating systems. It details four waves of attacks since its emergence on August 15, 2012, primarily against Saudi organizations. Shamoon, also known as Disttrack and other aliases, is linked to the APT33 actor group and affects various Windows operating systems. The malware operates by overwriting the Master Boot Record (MBR), rendering systems inoperable. Notable victims include Saudi Aramco and Saipem, with Aramco suffering damage to 30,000 computers. The post lists several hashes associated with Shamoon's components, such as Spreader.exe and Trojan.Filerase.",
"malware_name": "Shamoon"
}Updated 4 months ago